 |
| Source // Steam |
Hacking is a mystery to most of us. Something involving the Internet, logging into systems you shouldn't have access to, snooping around private files for all manner of purposes, then leaving via the backdoor. No, leaving a backdoor, before leaving by the front. Just leaving full stop, because they're tracking your every move and reporting it to the cyber police!
While the thrill of skirting/breaking the law might appeal to you, doing time for the crime will mean you won't get the chance to clear your gaming backlog for a long while, and nobody wants that to happen.
Enter Uplink, a hacking simulator where you bounce through systems and crack passwords and steal files all from the safety of a video game. This is all a video game, right?
 |
| Source // Steam |
Fun Times
Uplink starts off simply, taking you through a tutorial and pointing out where the help files can be found, before then dolloping seemingly everything upon you at once. It's like trying to make your way through a thick textbook, full of words you don't quite understand but have enough of a gist of to wing it and hope you don't get caught.
Let's take an example contract of deleting an important file on a faraway system.
Contracts are thrown up onto a bulletin board where you can pick and choose according to your abilities, and even haggle the price, should you think it worthwhile. Whatever contract you decide to accept, though, you're going to need to be prepared.
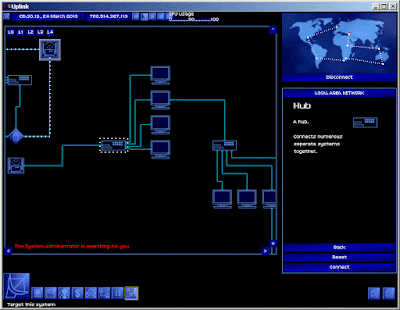
First of all, connecting directly to the target system is stupid. It is better to bounce around the Internet, from one computer to another, to make tracking you that much harder. While the game suggests three bounces, I decided to route my snooping through a handful of banks too, on the assumption that they have good security and will slow down anyone trying to find me.
Just to be clear, I have absolutely no idea if such a thing is actually going on, or if I'm doing all of this just to feel that little bit safer. I'm sure there's a gameplay mechanic in here. Why wouldn't there be? Anyway, the chain of connections at the ready, it's time to hit the target system.
The first line of defence for a system is a password, and while some credentials can be found and typed in, most of the time you'll need to run a program to crack a password. Uplink has your physical PC 'connect' to a gateway PC before starting the chain, and this gateway PC is the one you'll improve in-game to increase your security or upgrade your capabilities. You might give it more memory so you can steal larger files, or increase its speed so that you can run bigger, better programs.
For now, on a dinky little PC, all we can really do is juggle the CPU usage of our programs. Always running a Trace program allows you to be alerted to your target knowing something is going on, but it doesn't need to hog the CPU, especially while you're trying to crack a password. Give the password app all the processing power it needs, and you'll be into the target system in no time.
I didn't know the ins and outs of these mechanics, but I liked being able to control what I wanted to do, largely when I wanted to do it.
Once in, we need to find what we want and get on with the job of deleting it. Luckily, systems in Uplink are very hacker-friendly, and we'll be browsing files in seconds. While there are other areas of the system to play with, the File Server is our primary destination.
Checking our contact's message about what they want to be done, we load up a program to delete files and carefully select the right target. Within seconds, we've scuppered some poor souls chance of whatever that file would have allowed them to do. Score one for us hackers. It's time to inform the client we've succeeded and then get out of here.
But we're not quite done yet. Someone is likely to know we've been up to something fishy if their files are gone and the logs point, one system at a time, all the way back to us at home. We're going to need to mask our presence as best we can.
Frustrations
It is at this point where I hoped the tutorial was clearer, and the helpful information made a little more sense. Deleting a log file to hide which computer connected to the target makes things harder to trace. I get that. But removing a log file leaves a gap which says 'log deleted', or words to that effect, which is still a bit of a red flag to onlookers.
There are programs and updates to those programs that you can buy throughout the game, so long as you have the money, and a Log Modifier was one of my earlier purchases, allowing me to change the logs instead of deleting them outright.
Thematically, it makes a lot more sense, if a little fiddlier to get done, especially when up against the clock. In-game, it just resulted in me making Google the scapegoat.
I don't know what this does, but it feels like if I can do it, I should do it. After some light reading and a YouTube video, one strategy that supposedly comes close to game-breaking is to connect to one of the starting networks and bounce around the world from there, doing your job before coming back to this starting network, inexplicably one of the strongest and easiest to access systems in the game, and just deleting the log files of your connection to that first system.
Does it make sense? I suppose, yeah. How was I meant to learn that? Trial and error? It was most likely trial and error.
I played Uplink for a good hour or two, slowly working my way into more exciting contracts, like changing student records, for example. Sometimes the client didn't like how I worded the alterations, and sometimes I'd spend too long in a system that I would be kicked out after having been traced.
In those instances, I'd get an email about snooping around and being fined. If I don't pay the fine, expect a knock on the door. Yuh-huh. Sure thing. Hackers ignore those emails, right?
Oh. I guess my employers weren't kidding when they say 'if you get found out, we don't know you, you might as well not exist. Also Game Over'.
 |
| Source // Introversion |
 |
| Source // Introversion |
 |
| Source // Introversion |
Final Word
From more or less the start of Uplink, I was on board. I liked the idea of breaking and entering systems. I liked the thought of hunting around for the right file, or tampering with one or just setting up a system for future use, but what I got was somewhat repetitive and a little dull, certainly at first.
Copying or deleting files just proves you know your way around a system. I understand that simple contracts like that need to exist so that you can get a bit of money and some experience and so on, but they really are all you'll be doing for a while. When you get better, more exciting tasks start coming in, which will challenge your abilities against the clock, but if you slip up once, you run the risk of losing progress thanks to the 'one mistake and you're out' nature of the game.
If you know what you're doing and what upgrades you want, you can supposedly hit the ground running and be into the good stuff in next to no time, but I don't know what I'm doing, for the most part, and Uplink doesn't play too well with people who don't know what they're doing.
But I want to play it again, obviously. It's fun. I have no idea what I'm doing, but I like the thought of it. My pathetic score screen showed that I ruined the lives of 0 people. Damnit, I want to destroy at least one...
How to go about that? I suppose finding a guide, studying it, following that dense textbook to the letter would be a good start because if I don't, one wrong click could send me to that game over screen. Tense, sure, but I'd like just a bit of wiggle room. And that flame GUI, damn. I want to rice my system too. It'll make it perform faster, right?
If you've wanted your Sci-Fi RPG minigames to be expanded upon, then Uplink might grab your attention. I wonder if there's a plot to uncover. Can we do any real detective work, or are we just in it for the money? So many questions, I just need to go back and play it.
Fun Facts
You name the hacking film, there's probably a reference to it buried in Uplink.
Uplink, developed by Introversion Software, first released in 2001.
Version played: PC, 2001.













